IN THE BOARDROOM":
CEPS CSP. Founder
Tacon 1
SecuritySolutionsWatch.com: How would you summarize your mission statement & core philosophy.
Dustin: Our mission is to deliver exceptional service by treating our clients as true partners rather than just customers. We tailor every engagement to the client’s unique needs, fully integrating their objectives into our team—and embedding our team into their operations. For too long, the security industry has relied on minimal standards and a one-size-fits-all approach. We are committed to redefining that standard entirely.
SecuritySolutionsWatch.com: May we have a brief corporate history of your firm, Tacon1.
Dustin Typically, a client is either a law firm or employer. A law firm is often attempting to track down assets of a person, whether living or deceased, in order to adjudicate the property in an estate or trust or pursuant to a court order in any other judicial proceeding. Quite often, identifying and certifying the whereabouts of an heir in the case of executing the provisions of a will may avoid probate. Alternatively, if the background investigation uncovers proof that the heir is deceased, then that at as well can speed up the process of distributing or retitling the assets in an estate or trust.
> More
Founder
MARTELL TRAINING GROUP, LLC.
SecuritySolutionsWatch.com: :This wildly-popular video with over 940,000 views about “JUGGING: The New Ambush Robbery Trend You Need to Know About” is so very timely and important. Please tell us more, Steve, about JUGGING!
Stephen: Jugging is a form of robbery where criminals watch victims leaving banks, ATMs, high-value stores, or even tech retailers. They look for people handling cash, withdrawing money, or carrying valuable items, and then follow them to a secondary location where they feel hidden enough to strike. What makes jugging so dangerous is its simplicity. It relies entirely on:
• Predictable human behavior
• Victims who think the risk ends once they leave the bank
• Attackers who are patient and observant
My video resonated because people recognized how easily this could happen to anyone. Jugging isn’t just a big city problem; it’s happening in suburbs, grocery store lots, pharmacies, and retail centers across the country. The takeaway is this: most people never realize they’re being targeted—until the very end. Learning how to notice surveillance, route changes, and behavioral cues can prevent the attack entirely.
Notwithstanding the state requirements, routine database inquiries of Arizona state or county websites as well as making requests for police records is available to anyone and no license is required.
> More
President
Security Strategies Today
SecuritySolutionsWatch.com: :We’ve seen that you offer various professional services, including on-site threat assessments, foreign travel country briefings and private investigations. Can you tell us a little bit more about private investigations?
Steve Cocco: Of course. We conduct private investigations under license from the Arizona Department of Public Safety. These investigations pertain to all private investigative inquiries conducted within the state of Arizona. These can include inquiries about property, current or past assets, estate heirs, probate matters and background investigations. It’s important for the potential client to understand that a license from the state is required in Arizona in order for a person to use the title of private investigator and for a company to state that it offers private investigations. Always ask for the PI license number and check on line with Arizona DPS for the current status of the licensee.
Notwithstanding the state requirements, routine database inquiries of Arizona state or county websites as well as making requests for police records is available to anyone and no license is required.
SecuritySolutionsWatch.com: Who is the typical client that requests a background check?
Steve Cocco: Typically, a client is either a law firm or employer. A law firm is often attempting to track down assets of a person, whether living or deceased, in order to adjudicate the property in an estate or trust or pursuant to a court order in any other judicial proceeding. Quite often, identifying and certifying the whereabouts of an heir in the case of executing the provisions of a will may avoid probate. Alternatively, if the background investigation uncovers proof that the heir is deceased, then that at as well can speed up the process of distributing or retitling the assets in an estate or trust.
> More
 Michael A. Silva
Michael A. Silva
Principal
Silva Consultants President
International Association of Professional Security Consultants
The IAPSC Annual Conference is the one security industry event that is specifically tailored to the practice of independent security consulting and should not be missed if you are a security consultant or are thinking about becoming one. The conference includes educational sessions that help you to keep up with the latest security practices and technology, opportunities to develop strategic relationships with other consultants, and the ability to exchange ideas with some of the leading practitioners in the consulting profession. This year’s conference includes a risk assessment workshop and sessions on school security and emergency preparedness, the use of Artificial Intelligence (AI) in security, business growth tips for consultants, human trafficking, weapons screening, expert witness testimony in court, and consulting in casino and gaming security. The conference also includes exhibits and presentations from some of the leading providers of security products and services.
> More
Founder & CEO
Awareity
SecuritySolutionsWatch.com: Thank you for joining us today, Rick. One will read on Awareity.com that “Pre-Incident Prevention is the most effective, most forward-looking solution for improving people’s safety, trust, and freedom to go out and about. Pre-Incident Prevention involves people recognizing and utilizing the Pre-Incident Indicators exhibited by At-Risk individuals so Pre-Incident Intervention actions can be taken before the At-Risk individual(s) escalate and show up ready to execute their plan.” We couldn’t agree more!
Before we talk about Awareity solutions in much greater detail, in recent days there were tragic headlines once again regarding shootings at Florida State University, a Dallas Texas High School, and home invasion at the residence of Pennsylvania Governor Josh Shapiro. Details are still coming in but what are your thoughts, Rick, regarding pre-incident indicators that may have been missed in these tragic events?
Rick Shaw: From the early releases of information, each of the attackers and/or evildoers seemingly were known to be at-risk individuals before the attacks. This was due to exhibiting pre-incident indicators such as red flags, historical and concerning behaviors, and other warning signs. What we do not know at the time of this response, is which silos (students, faculty, family, friends, law enforcement, social media, mental health, city/county agencies, incident reporting options, systems, and other silos) the pre-incident indicators and behaviors were scattered across.
Silos are common recurring problems where pre-incident indicators and other information existed BEFORE the attack but were scattered so the whole story for each at-risk individual was not seen BEFORE the attack and pre-incident prevention actions not taken. When the existing pre-incident indicators are shared after the attack, headlines and leaders say things like they didn’t connect the dots and lawsuits point to negligence due to actions that could have been taken if the organization had connected the existing pre-incident indicators in the silos.
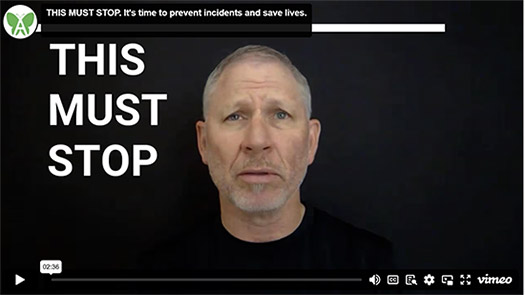
THIS MUST STOP !
We have heard these words before from:
Governors, Mayors, Chiefs of Police, CEOs, students, children and parents
WE CAN SAVE LIVES ! WATCH THE VIDEO HERE !
> More
Chief Operating Officer
SAGE Integration
John Nemerofsky: SAGE Integration is dedicated to providing enterprise-level security solutions tailored to the needs of each client. We specialize in access control, video surveillance, intrusion detection, AI technologies, and cybersecurity solutions, integrating these technologies into a seamless security infrastructure. In 2024, we added a security fence company, SAGE Fence, to address critical infrastructure clients' needs.
We serve a variety of industries, including commercial real estate, healthcare, financial institutions, manufacturing, critical infrastructure, education, and large-scale corporate enterprises. Our clients require robust, scalable security solutions that not only protect their assets but also ensure compliance with industry regulations and evolving security threats.
SecuritySolutionsWatch.com: We understand that SAGE has a significant strategic relationship with Honeywell. Care to elaborate?
John Nemerofsky: Sure. Our partnership with Honeywell enables us to bring cutting-edge security technologies to our clients. Honeywell's security solutions, combined with our integration expertise, enhance situational awareness and operational efficiency. This collaboration ensures our clients receive a best-in-class security solution tailored to their industry-specific challenges.
SecuritySolutionsWatch.com: Congratulations on your appointment, John, as a member of PSA Board Of Directors. We recently had the pleasure, and the honor, of also chatting with Matt Barnette, PSA President & CEO, “In The Boardroom” . Please tell us more about the special relationship between SAGE Integration and PSA.
John Nemerofsky: SAGE Integration greatly values its partnership with the Professional Security Association (PSA). Our associates are actively engaged in numerous PSA committees, which cover a wide range of areas including Sales, Service, Operations, Leadership, Managed Services, Women's Committee, New Generation Leaders, Purchasing, and CAD. This involvement ensures that we stay at the forefront of industry trends and contribute to shaping the future of our sector.
WATCH THE SAGE VIDEO:
What is your Duty of Care?
> More
 |
Jeff Wood VP of Sales North America |
 |
Jeff Thomas Regional Sales Manager |
 |
Gregg Gross Regional Sales Manager |
SecuritySolutionsWatch.com: Why is Wavestore’s participation in the Salto Partner Summit so significant?
Jeff Wood: The Salto Partner Summit is an important platform for fostering collaboration and sharing insights on the future of security technology. As a Sponsor, Wavestore is committed to building solutions that bring seamless interoperability between access control and video management systems. Our integration with Salto Space allows security teams to automate the display and retrieval of access control data with real-time video footage, enabling faster response times, improved situational awareness, and better overall security management.
Wavestore’s open-platform VMS is designed for seamless, real-time security integrations without the complexity of traditional SDK-based approaches. Many systems rely on multiple third-party platforms to connect access control with video, leading to delays and extra costs. Wavestore integrates directly with Salto Space, capturing events instantly and giving security teams immediate visibility instead of waiting for slow SDK-driven communication. Deployment is fast, simple, and significantly more cost-effective without the need for extra licensing fees. Best of all, it works with your existing cameras. We’re excited to showcase this powerful integration at the event and connect with partners looking for smarter, more efficient security solutions.
> More
CEO
Wavestore
SecuritySolutionsWatch.com: What does 2025 look like for Wavestore, and how do you see the company redefining the role of security solutions in a rapidly changing world?
Sam Shalaby: P2025 marks an exciting chapter for Wavestore as we continue to redefine what it means to deliver truly integrated and intelligent security solutions. Our vision is to lead the way in offering an unparalleled end-to-end experience, seamlessly combining advanced cameras, robust VMS, high-performance servers, and the growing integration of access control into one cohesive, future-proof ecosystem.
As the industry evolves, we recognize the importance of staying ahead of emerging trends like IoT integration, AI-driven analytics, and cybersecurity. At Wavestore, we see security systems not just as tools for protection but as platforms for smarter decision-making and operational efficiency. Our VMS will empower organizations with real-time insights, predictive analytics, and an unmatched ability to scale as their needs grow.
Sustainability is also at the core of our roadmap. We are committed to developing energy-efficient software solutions that reduce the environmental footprint of security infrastructures. From optimizing server performance to supporting cloud-based storage and hybrid solutions, we aim to deliver security that’s both effective and eco-conscious.
Customer-centric innovation drives every decision we make. By listening closely to our partners and clients, we are continuously enhancing our solutions to meet real-world challenges – our latest Health Monitor update being an example..
> More
 |
Jeff Wood VP of Sales North America |
 |
Kevin Baldwin Head of Marketing |
 |
Fadi Hajjar Director of Sales Canada |
 |
Paul Sarnese CHPA, MSE,MAS,CAPM |
 |
Domenic Gallelli MS, CPP, Director of Business Development |
 |
Jennifer Schmitz MSN,EMT-P, CEN,CPEN, FNP-C, NE-BC, V.P. of Client Engagement for Engage Powered by ENA |
We recently read that the state of Virginia is now mandating that hospitals and emergency departments conduct a risk assessment of the environment and provide trained security staff within the Emergency Department at all times.
Today, we are joined by Paul Sarnese, CHPA, MSE, MAS, CAPM, Owner of Secured & Prepared Consulting and Jennifer Schmitz, MSN,EMT-P, CEN,CPEN, FNP-C, NE-BC, Vice President of Client Engagement for Engage, Powered by ENA, and Domenic Gallelli, MS, CPP, Director of Business Development at Valentis to discuss the impact of this new law.
Read about the new law here: Virginia Law Requires Every Hospital with an Emergency Department to Establish a Physical Security Plan Using Industry Standards (americanbar.org)
> More

 The Kindness Games
The Kindness Games
Co-founders, Tim Wenzel
and Lee Oughton
SecuritySolutionsWatch.com:
One will read at on your site at TheKindnessGames.com, that, "The Kindness Games was started as a way to counter the disruption, hate, and discontent that has engulfed our world during the COVID-19 Pandemic and the ensuing spike of racial tensions and civil unrest. We aim to heal our relationships and communities through targeted #kindness." Care to elaborate?
Tim Wenzel and Lee Oughton: In the fast-paced realm of security professionals, where the primary focus often centers around safeguarding assets and managing risks, a heartening movement has emerged - The Kindness Games (TKG). What started as a simple gesture among security professionals to acknowledge individuals who have positively impacted their careers swiftly evolved into a global phenomenon, transcending boundaries and spreading the message of kindness and unity.
The inception of The Kindness Games stemmed from a genuine desire to recognize the unsung heroes within the security industry, those individuals who selflessly extended a helping hand or offered invaluable guidance along the career paths of their peers. It began as a means to express gratitude and appreciation but soon blossomed into something much greater.
As the movement gained momentum, it caught the attention of individuals from diverse backgrounds and professions. The essence of TKG deeply resonated with people, sparking a collective desire to extend kindness beyond the boundaries of their immediate circles. It wasn't merely about acknowledging the contributions of others; it was about nurturing a culture of inclusivity, healing communities, and effecting positive change on a global scale.
> More
Co-founder, President, Exec Chair of the Board
Athena Security
SecuritySolutionsWatch.com: Thank you for joining us today, Lisa. Athena Security will soon be exhibiting some exciting cutting-edge tech at ISC West on April 9-12, in Las Vegas. But before getting into that, can you talk briefly about your background?
Lisa Falzone: I've always believed in the power of technology, and so I've built my career on leveraging technology to move industries forward. I actually started in commerce, not security. With Revel Systems, I built the first enterprise iPad cash register, and we scaled up to a 700-employee international company partnering with IBM and Apple.
SecuritySolutionsWatch.com: And a very successful one. You've been featured in Forbes Magazine 30 under 30, Fortune Magazine 40 under 40, Tech Crunch, Business Insider... So why the shift to security?
Lisa Falzone: The short answer is, I became a mom. Like most parents, I was dismayed by the growing problem of school shootings. I wanted to give my daughter and son a safer world, and I felt like I had the ability to do something about it. So I founded Athena Security as a way to address the issue, and use my passion for technology to address the growing need for more advanced security measures. We're creating innovative solutions like the A.I. Athena Weapons Detection Solution that I really think can make a difference and save lives.
SecuritySolutionsWatch.com: Athena Security has recently announced the addition of an "Evasion Detection" feature, using AI to identify visitors who attempt to bypass the screening process. Care to elaborate?
Lisa Falzone: Sure. In crowded entryways, visitors sometimes try to skip the screening process for various reasons. Identifying these evasions is essential for effective security because the world's most advanced weapon detection system still doesn't work if people can just bypass it. Our latest update includes an Evasion Detection AI which automatically locates anyone attempting to get around the weapons detection portal, and notifies the guard on duty or can escalate the alert to anyone else who needs to be aware of the evasion.
> More

 Paul Sarnese,
Paul Sarnese,
CHPA, MSE,MAS,CAPM
and Mitch Gesinger,
MSN, RN, CJCP, CPHQ
from
Secured & Prepared Consulting
SecuritySolutionsWatch.com: Thank you for joining us again today, Paul and Mitch. It’s aways an honor to speak with the past President of the IAHSS (International Association for Healthcare Security and Safety). Welcome Mitch. Congratulations on the growth and expansion of your consulting firm Secured and Prepared Consulting. We read with great interest your recent LinkedIn post regarding 2023:
2023 was a great year for Secured & Prepared Consulting speaking engagements! Our team had the honor to share our knowledge and experience with several organizations who are leading efforts to reduce violence in healthcare. We were able to speak in front of and with all of the following agencies.
- International Association for Healthcare Security and Safety (IAHSS)
- International Hospital Federation IHF Secretariat
- American Hospital Association
- American Society for Health Care Risk Management (ASHRM)
- New Jersey Hospital Association
- Massachusetts Health & Hospital Association
- Johns Hopkins University School of Medicine
- New Jersey Primary Care Association
- New Jersey Emergency Preparedness Association
- National Healthcare CFO, CXO and HR Summit
That’s quite an impressive list! Care to elaborate, Paul, regarding the some of your 2023 projects and success stories?
Paul Sarnese: Secured and Prepared Consulting had a fantastic year. Not only did we have several speaking engagements, but we also had the opportunity to perform multiple workplace violence assessments for several Health Systems, Academic Medical Centers, Community Hospitals, Critical Access Hospitals, Home Care, Long Term Care, and corporate offices. The feedback that we received from those organizations was incredible. The reason it was so incredible is because Secured and Prepared Consulting is different than its competitors.
> More
RN, BSN-CEO
Cortex GOLD, TACTBook
’We are honored to have been accepted by the Institute for Homeland Security and Sam Houston State University for their 2024 Spring Research. We will be studying the impact that a Standardized Workplace Violence Training for Healthcare Workers and Healthcare Security would have on critical infrastructure support for healthcare. Early adopters will be considered for future grants and research opportunities as they become available. This will allow smaller, lesser funded organizations to access the training and support they really need. To get more information on this incredible opportunity please visit our website. I have talked to some nurses doing research at Yale and Mass Gen on violence projects and I am excited about offering our support there. People are really excited about our potential to use Training and research in schools. We even had a local business offer to donate a building for 6 months free lease to house our Veterans Vocational Training Center and Technology Innovation Gallery.
> More
Vice President of Sales
AMAG Technology
SecuritySolutionsWatch.com: Congratulations, Jody, on nearly two decades with AMAG! Thank you for joining us again today. So much has changed since we first featured you "In The Boardroom" several years ago. Before we discuss today's main topic in greater detail, the AMAG solution for organizations who are faced with the challenge of finding a replacement for their 'sunsetted" Casi Rusco access control systems, please share with our readers your current role with this project.
Jody Ross: In my nearly two decades with AMAG as a sales leader, I"ve spearheaded several sales initiatives including our first Symmetry SR initiative about 10 years ago. Currently, among many responsibilities, I manage and support several large customers who have made the migration to Symmetry SR.
SecuritySolutionsWatch.com: The video here describes the situation very well. We understand that AMAG is stepping up once again, as you did several years ago, to provide a simple, cost-effective migration solution. Please recap for us here the Casi Rusco situation.
Jody Ross: We"ve always been here supporting" As you may recall, in 2011 the manufacturer of the Casi Rusco - Picture Perfect system announced the end of support for the solution. This left many customers who had invested in that platform in a predicament. This year, another well-known manufacturer of Casi Rusco replacement boards announced the end of life for their panels, which, once again, has left customers in a bind. We are proud to say that AMAG still offers our replacement solution, Symmetry SR and will continue to do so in the future. Our customers can count on us to support them now and into the future.
> More
President - CEO
Strongbox Security Services
We have had great feedback from our School Security Division. We currently provide Security Guard services for four area schools including a vocational school, a preschool, and two High Schools as well as an amazing Summer program for student-athlete development. I've been told by client contacts that our presence on campus at each site have put faculty, staff and parents at ease, knowing that there is a professional and capable security presence protecting what matters most to them, the children. In addition to schools, we provide security to various religious institutions and other businesses. Our School Security Division is what I am most proud of.
> More
Director of Sales, Latin America
and Caribbean
AMAG Technology
Data Centers are a new and critical vertical for us as we have several large customers in this market. We are seeing US/European companies investing in either buying existing data centers or building new ones, and that has expanded into the LatAm region. AMAG's Symmetry Security Management System offers a single point of entry to all the security software and hardware in each facility, which can be controlled either locally or from a central control center. The objective is to have one screen where you can see all the Cameras, Access Control, Audio, Radars, Visitors and so on, independently of the hardware brands. Our Symmetry system also helps manage compliance requirements, which are different for each country.
AMAG's Symmetry solutions can operate in nearly all vertical markets. We can help our customers with their security challenges by providing an integrated security solution. We have integrations with over 100 technology partners and are able to provide many options for our customers. We specialize in Finance, Food Plants, Restaurants, Oil & Gas, Healthcare, and Data Centers, but also work in Education, Transportation, commercial/Real Estate, Ports, plus many others.
At this moment we are implementing our Symmetry Security Management platform in one of the top LatAm companies in more than five countries where from a single control center they will manage +150 restaurants, food plants, malls, buildings and other facilities, not only from an access control point of view, but their system will also include audio, video, visitor management along with several technology partner integrations to provide a complete system. Again, our main goal is to be the trusted advisor for our clients who are looking for an open and integrated solution.
> More
Chief of Analysis (COA)
TAM-C
TAM-C Solutions is the leading geopolitical intelligence and security company with a history spanning over two decades. Established in 2003 simultaneously in the United States and Israel, it has evolved into a multinational firm with headquarters in multiple locations across the United States, Israel, the UAE, Bahrain, and Saudi Arabia. Once a boutique company, focused on actionable intelligence and led by several veteran security specialists, TAM-C has since transformed into the fastest-growing security and intelligence organization worldwide, boasting various departments and divisions, ranging from asset security to due diligence operations and on-the-ground intelligence and protection services.
TAM-C is the premier source for custom geopolitical intelligence solutions for many international corporations and governments. Our lens of critical analysis takes into account an array of client-centric factors, ensuring that the intelligence provided is not only accurate and insightful but also perfectly aligned with the recipients’ unique and dynamic requirements. As a result, we enable our partners to make informed decisions that drive success on a global stage.
Our operations, however, do not end with intelligence collection. Although TAM-C was not initially established to provide on-the-ground intelligence, protection, and crisis management services, our distinctive expertise in these fields required us to assist our clients and the general public during times of emergencies. TAM-C now operates a large-scale division for executive protection and asset security on the ground, supported by intelligence collection operations. We do not hesitate to make these resources available to the general public when they need us, as we consider it the least we can do for populations during times of crises.
> More
We sat down with Tim Gilman, CEO, Cyber Armed Security™, who spoke to us about the innovations his company is undertaking in addressing cyber threats and their new partnership with Steve Cocco of Security Strategies Today.
Cyber Armed Security™ is a pioneering force in the realm of cybersecurity, where ethical hackers unite to safeguard the digital landscape. Our journey began when a group of highly skilled hackers, recognizing their exceptional talents on global training platforms, came together to form a formidable cybersecurity enterprise. What started as a passion quickly evolved into a thriving venture that has expanded its horizons into intelligence services, drawing expertise from veterans of intelligence agencies and military regiments, including electronic warfare specialists.
Today, we proudly stand as a rapidly growing cybersecurity entity, poised to diversify our portfolio with the imminent launch of two to three new brands. Our expansion strategy encompasses ventures into private investigations for businesses (B2B), consumer markets, and even polygraph testing. Additionally, we are strengthening our presence in private security services, executive protection, and global operations, harnessing cutting-edge technologies such as big data analytics, artificial intelligence (AI), and open-source intelligence for enhanced security and advanced threat detection.
Our penetration testing services gain a distinct edge through teamwork. Recognizing that most real-world cyberattacks are orchestrated by groups, we deploy diverse skill sets by having at least two to three testers on every project.
> More
Vice President - Technical Services
AMAG Technology
SecuritySolutionsWatch.com: We had the pleasure of speaking recently with AMAG's new President, David Sullivan and also with Paul Edwards, AMAG's Executive Vice President of Business Technology. In both discussions, AMAG's customer-first culture was stressed as a top priority. David Sullivan recently said, "Instilling a customer-first culture is at the forefront of my mission as president, and our entire organization continues to work hard to support all of our channel partners to the greatest extent possible." Please share with us, Ryan, how this guiding philosophy of "customer-first" ties into your current role, and the goals for your team, such as lower call-hold times.
Ryan Howarth: For Technical Services, this means examining our internal processes and using metrics to measure several KPIs to see where we need to improve or change. We are also looking at what we can do to add further value to our services with the goal of continuously improving how we support our customers. One such improvement was utilizing technology to bring the team together, allowing us to increase the hours of service that we provide and improving our average call hold times, which today are 1m15s for the year.
> More
Managing Partner
CSI-Secure Solutions
Surveillance is our primary service offering especially in workers’ compensation and personal injury cases. We also provide skip tracing services of claimants who have committed insurance fraud and once found we conduct comprehensive background investigations inclusive of in-depth social media Research. Often times with social media we can prove that the claimants we are investigating are exceeding their physical capabilities when they are supposedly injured or unable to have physical competency. We also may research during the discovery process documentation showing that the claimant has prior fraud cases associated with him/her. The attorneys and insurance carriers who retain our services may request that we interview neighbors, colleagues, associates and other employees known to the claimant that can give testimony relative to fraud being committed by the claimant.
> More
Executive Vice President
of Business Technology
AMAG Technology
Previously, security solutions were on isolated networks, but with the convergence of technologies and the cyber threat, IT is now a key stakeholder in all decisions and the ongoing management of a solution. It is important that the security industry is staying as up-to-date as possible (which can be a challenge) with the latest threats. The homograph attack is an example of how vigilant people need to be, as by using the Latin character "a" is replaced with the Cyrillic character "a" but are actually different, so a user could receive an email or click a link that looks valid, but in fact is a completely different site hosted by the threat actor. We are rolling out a new program internally this year to ensure we provide our staff with meaningful, digestible information on a regular basis which will help protect not only AMAG staff at work but our staff in their personal lives as well. Through this knowledge, our staff will be able to discuss cybersecurity with our partners and customers in a relatable manner and bring in internal subject matter experts as required into conversations.
> More
President
Security Strategies Today
We are excited about our new partnership with Cyber Armed Security. This UK-based company is composed of a global team of ethical hackers with over 20 years of experience in cyber security. Its operatives come from ex-military, ex-intelligence, Interpol, and the British army. Their intelligence-gathering activities enable them to conduct cyber-based attacks and test the weaknesses and vulnerabilities of clients, which is not feasible without a robust intelligence element. The company merges cyber security and physical security by utilizing OSINT (open-source intelligence) and leveraging partnerships, such as with Security Strategies Today.
> More
 Michael A. Silva
Michael A. Silva
Principal
Silva Consultants President
International Association of Professional Security Consultants
The IAPSC Annual Conference is the one security industry event that is specifically tailored to the practice of independent security consulting and should not be missed if you are a security consultant or are thinking about becoming one. The conference includes educational sessions that help you to keep up with the latest security practices and technology, opportunities to develop strategic relationships with other consultants, and the ability to exchange ideas with some of the leading practitioners in the consulting profession. This year’s conference includes a risk assessment workshop and sessions on school security and emergency preparedness, the use of Artificial Intelligence (AI) in security, business growth tips for consultants, human trafficking, weapons screening, expert witness testimony in court, and consulting in casino and gaming security. The conference also includes exhibits and presentations from some of the leading providers of security products and services.
> More
Chief Executive Officer
MetAlert
(formerly GTX Corp)
OTC: MLRT
We are excited to be moving forward under the MetAlert brand. GTX no longer represented everything that we do and our vision of the future. In the beginning our focus was primarily on tracking and Global Trek Exploration, abbreviated as GTX made sense. In recent years, our Company has been focusing on solutions that transform people's lives, with this transformation we felt the need for a change. Our vision is that in the near future, the people that use our products and services will live longer, healthier, and higher quality lives. This will happen because our products will collect vital information in real time, send it to the cloud, where that data can be analyzed and through our backend A.I. and notification platform, that data will be sent to doctors, first responders, caregivers, or family members. Imagine a 65-year-old man, that has a mild heart attack, doesn"t really think much of it and the next day goes out and plays tennis or golf and has another heart attack. Our products would be able to detect that, send the information to a first responder including the address of where that person is. This scenario is a life saver for that individual and we believe MetAlert speaks to that vision.
> More
Director of Sales " EMEA
AMAG Technology
Access control systems have always been great repositories of big data"every time you swipe your card or present your phone at a door, you are creating data. But very little has ever been done to analyze that data"until now. AMAG has developed a machine learning algorithm that learns what normal behavior is for an access control system" it learns when you usually arrive at the office, which door you enter the facility via and where you go next. So if you suddenly start arriving earlier and going to different locations, which you may still be allowed access to, the system will recognize that as "abnormal behavior." There may be perfectly genuine reasons for the observed behavior, but the AMAG solution provides you with that insight" it gives you an early warning of potentially nefarious activity so you can make a better, more informed decision.
> More
CEO
Prosegur
Organizations are in various states of assessing their workforce needs as they start to bring employees back to the office. Every company is looking at the situation through a prism of their own needs. From a security perspective, I tell our clients that they need to have a heightened awareness of the mental state of their staff. The pandemic has increased tensions and stress levels. For example, some employees are stressed about rules around vaccinations and mask-wearing in the office.
If you are in charge of security, it’s now more important than ever that you carefully evaluate your people, process, and technology in this new normal and be prepared for potential disruptions. Some of these situations could escalate into violence. Secondly, we have to consider the security of remote workers. What security risks are in their home? Is there the possibility that your workers are leaving sensitive documents in the open? Are they locking their home office? Do they have a shredder? Are they following good cybersecurity hygiene? Or are they creating a massive vulnerability for someone to access sensitive corporate information?
> More
Director of Sales
AMAG Technology
AMAG’s unique value proposition is one of the main reasons I joined the company. There are many companies that offer access control, video or identity management solutions. What makes AMAG unique is that we offer a total solution that is developed in-house. We manufacture our own access control software and hardware, visitor management and identity management systems. Manufacturing our own hardware and software allows us full control over feature enhancing upgrades, ensuring continuity of supply for the long term. Our system is completely scalable, meaning a Symmetry Security Management System can operate in a small business or secure a large company, even with locations around the world.
Another key differentiator is AMAG incorporates an open architecture into its Symmetry solution. Symmetry integrates with ANY technology on the market, including other access control systems. Integrating with other access control systems is important for large enterprise customers who acquire companies and take on the responsibility of managing the new company’s existing access control systems. Integrating with those new systems simplifies the overall security management and lets the company issue one card for all systems. In addition, our support team provides complete support for all third-party products integrated with Symmetry. This is a huge relief for our customers who don’t want to jump around to different manufacturers when they have issues.
> More
Global Director of Innovation and Product Development for Security
Prosegur Global Risk
Prosegur’s strategy is focused on two important concepts. We must Perform by offering our customers the very best service in our traditional businesses such as guarding. And we must Transform by offering our customers new and innovative security solutions that are unique to Prosegur and the security industry. Our innovation strategy is focused on new product development. When developing new products we analyze their desirability, feasibility, and scalability. But we don’t just concentrate on the traditional security industry. We look to adjacent industries that we know are equally important to our customers, such as business continuity and safety. And our Security Operations Centers (SOCs) around the world are the hub of innovation for our company.
> More
Director of Business Development
AMAG Technology
My business development team at AMAG Technology is 100% dedicated to the security consultant community and architects and engineers. This community is the backbone of the security industry. They have power, much more than meets the eye, to drive some of the most meaningful work in the security space. The industry works collectively as a wheel that keeps churning with the ultimate goals of saving lives and protecting properties and assets. We have security end users that have a business to run and security plans to operate and execute on. We have technology developers, such as ourselves at AMAG, that provide innovative solutions the end user can rely on to optimize their security programs. And we have the systems integrators who bring the systems to life and maintain their health and long-term functionality. But what sets the wheels in motion is the physical security consultant.
> More
Managing Director
Imperial Capital
The traditional alarm monitoring market operates under a business model where high margin recurring monthly revenue is used to subsidize initial costs (primarily hardware and installation costs). The traditional model has been very successful in landing (typically for no upfront fee or a small fee up-front fee) and keeping long-term customers for years that pay monthly recurring fees. In the last several years, we have seen a surge in the IoT and Home Automation markets. The problem with IoT and Home Automation, while growing rapidly, is that they have lacked an integrated offering with a compelling service model thus, there has been limited recurring revenue.
We believe IoT and Home Automation providers are beginning to move to an Alarm Monitoring business model (with limited upfront fees but with the customers signing long-term contracts). This shift can be observed with recent companies like Latch Inc (LTCH " Not Rated) and Smart Rent (Not Rated) both offering services to multifamily facilities with high recurring fees (we will discuss Latch in further detail later in this report). We are also observing traditional alarm companies moving further into IoT and Home automation like ADT and Monitronics/Brinks Home Security experiencing solid growth and higher retention through a broader offering to its end user. Finally, we see multinational security companies like Prosegur expanding its offerings from guard/alarms/cash management to video monitoring and home automation to increase RMR or recurring monthly revenues.
> More
CEO & Co-founder
Digital Trust Networks Inc
A Covid credential presentation would be an excellent use case for what we are doing, whether it is a Covid test result or a Covid vaccination proof. A Service Provider like an airline before boarding, a rental car agency before renting a car, or a hotel before checking in, should be able to check the validity of the presented credential, that it belongs to the person who is showing it, that it is the latest data, that it comes from the actual source, and that the source can actually be trusted -- that it is a genuine facility, and not a fake credential provider. Digital Trust Network’s Digital Identity Interchange is a perfect vehicle to achieve this. Further, the issuing sources will be part of the value chain when the credential is verified. This system protects user privacy, invalidates fraudulent certificates and credentials, and provides the latest information.
> More
CEO & President
TECHEXPO Top Secret Cyber Security Summit
When the entire live in-person conference industry came to an immediate halt, my team and I quickly created a series of Cyber Security Briefings to help maintain its goal in educating executives called the “Power Hour”. Similarly to their live events they featured experts from The FBI, The US Secret Service and Dept. of Homeland Security / CISA. Hosted on one of the most secure and trusted virtual platforms, Cisco WebEx; these complimentary, invitation-only webcasts offered senior level business executives information on the latest cyber threats facing their companies as they worked from home during the peak of this pandemic. In addition they provided insight on best practices and technical solutions from top companies such as IBM, Google, Artic Wolf, Proofpoint, Mimecast, Duo Security, Check Point, Darktrace, KnowBe4 and more.
> More
VP of Products & Technology
AT&T Cybersecurity
Digital transformation - the movement of critical computing from the data-center to the cloud - is driving rapid changes in business models and network architectures. It also drives changes in how cybercriminals operate, making it easier for them to harvest data and launch automated attacks at scale. The mismatch between changes in cybercrime sophistication and the relative stagnation in cybersecurity approaches is apparent as organizations continue to suffer data breaches. According to a survey presented in AT&T Cybersecurity Insights, 88% of respondents had reported at least one type of security incident or breach in the last year.
The root cause? Dispersed networks, an explosion of data, disparate technologies, complex security operations present cybercriminals with gaps or “seams” in organizations’ security postures. Fighting cybercrime requires a coordinated and collaborative approach orchestrating best-of-breed people, process and technology.
> More
Managing Director and Founder
Allegis Cyber
Experience continually reinforces the reality that the human element is the weakest link in cybersecurity. This means the most important proactive strategy of all is to train everybody in a corporation - and I mean everybody - in good cybersecurity practices, along with their contractors and vendors. All employees should not only understand what is expected of them regarding company security policy and good online behavior, but also be trained to spot nefarious or suspicious activity and to conduct periodic tests to ensure best practices are followed.
> More
Managing Director
Blumberg Capital
One should think about security under the following framework:
Continuous authentication: 100% of fraud occurs inside authenticated sessions. This means that the login function is not really relevant anymore because fraudsters have found ways to bypass it, whether it is password, token or even a physical biometrics.
- Dynamic authentication: Most methods of authentication are static. Behavior by definition changes over time so one needs to deploy techniques that cannot be copied, stolen or otherwise used in a replay attack.
- Go beyond the endpoint. Applications and active sessions are incredibly vulnerable as fraudsters use social engineering scams and even phishing scams (where the legitimate person defrauds themselves under the influence of a fraudster).
- Recognize that humans are the weakest link and design systems accordingly. Thirty percent of participants will still open malicious emails within 30 minutes of phishing training. It only takes one person (the weakest link) to bring down an entire enterprise.
> More
 Carl Bradley, U.S. Navy (Ret.)
Carl Bradley, U.S. Navy (Ret.)
Information Assurance & IT Security Consulting & Intelligence Strategy
HP Enterprise Services,
U.S. Public Sector
There are three key challenges our clients face today. First, cyber threats are ever-changing and becoming more sophisticated by the day. Cyber terrorism and targeted cybercriminal activities are directly impacting both the public and private sectors. They are persistent and yet, based on our research into exploit trends in 2014, attackers continue to leverage well known techniques to compromise systems and networks. Many vulnerabilities exploited in 2014 took advantage of code written many years ago and adversaries continue to leverage classic avenues for attack against client-side and server-side applications. Anti-virus signatures only catch approximately 45 percent of cyber attacks—a truly abysmal rate.
In our review of the 2014 threat landscape, we find that enterprises most successful in securing their environment employ complementary protection technologies. These technologies work best when paired with a mindset that assumes a breach will occur instead of only working to prevent intrusions and compromise from the perimeter. So our clients’ security posture must be agile and responsive to better defend against threats —internal and external—in addition to vulnerabilities, in order to mitigate their risk...
> More
Chief Cybersecurity Officer
Carbon Black
Existing cybersecurity architectures are failing due to two macro trend cloud computing and mobility. The endpoint is inadequately secured and the adversary often has a footprint within one’s perimeter defenses. We must pursue a strategy of intrusion suppression wherein we can decrease dwell time and this detect, deceive, divert and hunt and adversary unbeknownst to the adversary. To achieve this an organization must: employ application whitelisting, employ an endpoint protection platform, establish a Hunt Team and roll out deception grids. Employ Deceptiongrids.
> More
BREAKING NEWS:
Homeland Security investigates sites in Minneapolis for "rampant fraud"
> More
The NASDAQ Cybersecurity ETF Looks Like One of 2026’s Best Investments
> More
Trump’s 8 biggest national security wins of 2025
> More
Apple Encryption and Data Protection overview...what you should know
> More
Zelenskyy discusses necessary security guarantees
> More
IBM warns of a critical security flaw that allows attackers to gain remote access
> More
Top 10 Most-Read Security News Stories of 2025
> More
Protestors killed by security forces in Iran
> More
The Top 10 National Security Jobs of 2025 and What’s in Store for the Year Ahead
> More
China warns satellites from Elon Musk’s Starlink are ‘safety and security’ risk
> More
There’s new leadership at the Defense Counterintelligence and Security Agency
> More
Two cybersecurity employees plead guilty to carrying out ransomware attacks
> More
Security concerns ahead of New Year’s Eve celebrations
> More
Trump warns of ‘hell to pay’ if Hamas doesn’t disarm in ‘very short’ time
> More
Multi-layered approach needed for building effective AI security governance
> More
Microsoft fixed 100+ security flaws in Windows and Office
> More
What do Putin and Trump each want from the Alaska summit?
> More
Check out the Apple Security Platform
> More
Research shows AI agents are highly vulnerable to hijacking attacks
> More
Trump delivers remarks on 90th anniversary of Social Security
> More
Roundtable focuses on school security
> More
Canada’s House of Commons Hit by Cyberattack Exploiting Recent Microsoft vulnerability
> More
Latest CISA cyber guidance urges organizations to inventory OT assets
> More
Hack of federal court filing system exploited security flaws known since 2020
> More
Zoom and Xerox Release Critical Security Updates Fixing Privilege Escalation and RCE Flaws
> More
Trump’s AI deals in the Middle East have security experts sweating
> More
Google testing stronger security measures
> More
Chinese solar tech poses 'chilling' threat to US electric grid, lawmakers warn
> More
Apple releases important security updates
> More
67% of Organizations Faced Cyber Attack in The Past 12 Months
> More
Coinbase Confirms DOJ Investigation Following Major Security Incident
> More
Demonstrators clash with security at Microsoft event in Seattle
> More
Secret Service, DOD, Coast Guard, Border Patrol applications surge under Trump
> More
Project Homecoming Charter Flight Brings Self-Deporters to Honduras, Colombia
> More
Why experts say you need to opt out of TSA facial scanning screenings, how to do it
> MoreRECENT HEADLINES:
US Embassy warns Americans of mass shooting threat> More
TeleMessage, the app that President Donald Trump's former national security adviser, Mike Waltz, appeared to use to archive his group chats, has suspended all services> More
National security investigation of pharmaceutical imports> More
The Hidden Security Risks of Data Exposure in AI-Driven Tools> More
Google Fixes Android Flaw Exploited by Attackers> More
Security in upscale L.A. apartments lax even after unsolved murder, tenants say> More
Cyber Security expert explains depth of Russian hacking group ransomware attack> More
Heightened security at Trump Towers> More
White House has asked U.S. military to develop options for the Panama Canal security.> More
Private Biden email address received sensitive security info> More
The Trump Administration will not cut Social Security, Medicare, or Medicaid benefits.> More
US FCC launches Council for National Security to combat foreign adversaries, focus on China> More
Using AI-Driven Cybersecurity Training to Counter Emerging Threats> More
Google Play Store to enhance security> More
Microsoft Warns of ClickFix Phishing Campaign Targeting Hospitality Sector via Fake Booking[.]com Emails> More
Lilly, J&J boosted spending on executive security after UnitedHealth shooting> More
Tesla facilities face wave of attacks as Elon Musk delves into politics> More
48% of Americans have received a fraudulent tax-related message> More
Chinese Hackers Breach Juniper Networks Routers With Custom Backdoors and Rootkits> More
Sam Shalaby, CEO, Wavestore, Discusses 2025 and Redefining the Role of Security Solutions In A Rapidly Changing World on NBC News.> More
Trump revokes security clearances of former officials who signed Hunter Biden laptop letter with executive action.> More
Top 10 2025 " Most Critical Cybersecurity Threats> More
The White House has unveiled a groundbreaking initiative to enhance the security of internet-connected devices in American homes.> More
AI Cyber Security Predictions 2025> More
AWS Releases Best Security Practices To Mitigate Ransomware Attacks> More
Security Alert Issued As 1 Billion Passwords Stolen By Malware"Act Now> More
Protecting the united states from foreign terrorists and other national security and public safety threats - executive order> More
Security expert weighs in on mysterious drone sightings> More
Metro districts bolstering security to help prevent school shootings> More
FBI Hacking Warning"More Bad News For iPhone, Android Users> More
The Cybersecurity and Infrastructure Security Agency (CISA) Warns of Adobe & Windows Kernel Driver Exploited in Attacks> More
Microsoft Teams Vishing Spreads DarkGate RAT> More
Almost 800 arrested over Nigerian crypto-romance scam> More
New Investment Scam Leverages AI, Social Media Ads to Target Victims Worldwide> More
2025 Physical security predictions from industry leaders> More
Iranian Hackers Use IOCONTROL Malware to Target OT, IoT Devices in US, Israel> More
Protecting Trump in a second administration presents unprecedented security challenges> More
FBI Seeks Public Help to Identify Chinese Hackers Behind Global Cyber Intrusions> More
Google Patches Two Android Vulnerabilities Exploited in Targeted Attacks> More
Beef Up Your Password Security Here...and NOW !> More
The prospects for economic security under Trump or Harris> More
Docusign API Abused in Widescale, Novel Invoice Attack> More
Hezbollah Walkie-Talkies Blow Up Across Lebanon in Second Wave of Attacks> More
Donald Trump Identifies Security 'Weakness' After Assassination Attempts> More
Let's Talk with #TEXASNIGHT2024 Founder Charles "Chuck" Andrews - Founder & Chairman of the Board "Friends of Chuck" - as seen on ABC News!> More
Second wave of deadly device explosions injures 300 in Lebanon> More
Google Chrome 129 Released With Fix for 9 Security Flaws> More
Hearing on Biden Administration Border Policy> More
Let's Talk with Global Counter Terrorism and Hostage Rescue expert Nir Yaniv Maman - as seen on NBC News!> More
Acting Secret Service denies agents knew of would-be assassin's perch on roof, says he's "ashamed" of Trump rally shooting security gaps> More
France Suffers Attack on Broadband Services Amid Olympic Games> More
Biden's cybersecurity legacy: "a big shift" to private sector responsibility> More
Paris Olympics Security Trains> More
Attack on train system highlights broad array of security threats to Paris Olympics> More
Border security could be Kamala Harris's 'achilles heel' in her fight against Trump> More
Poor security let hackers access 40 million voters' details> More
Millions of Websites Susceptible to XSS Attack via OAuth Implementation Flaw> More
Let's Talk with Greg Schneider, Owner, Battle Tested Solutions, About The Attempted Trump Assassination> More
Using Threat Intelligence to Predict Potential Ransomware Attacks> More
Biden to tighten national security, public safety asylum screenings> More
File Hosting Service Dropbox Breached By Cyberattack> More
National Security Agency warns against paying ransoms> More
Palo Alto Networks, Microsoft, Google, CrowdStrike, IBM announce major AI security news> More
Experts highlight progress, challenges for election security> More
Candian government hit by 'sophisticated cybersecurity incidents> More
$400 million boost in federal funds for security at places of worship> More
Cyber security event' impacts Ascension> More
Cybersecurity jobs available right NOW !> More
Microsoft: 87% of Organizations Vulnerable to Costly Cyber-Attack > More
Fighting disinfo is a 'vital US national security interest' > More
Cisco Completes $28 Billion Acquisition of Splunk > More
5 certifications that can boost a cybersecurity leader's career > More
Cybersecurity and Infrastructure Security Agency (CISA) hit by hackers, key systems taken offline > More
Border security deadlock heightens risk of government shutdown > More
IDF eliminates head of Hamas's internal security during Shifa hospital operation > More
Protecting Americans" Data and National Security > More
Fujitsu Hacked " Attackers Stole Personal Information > More
Tensions and desperation are growing on the border between Haiti and the Dominican Republic > More
Cybersecurity Legislation Seeks to Protect America's Food Supply Chain > More
New 'national security threat' - Russian nuclear weapons in space. > More
Best new home security systems of 2024. > More
Google launches a slew of AI initiatives to enhance cybersecurity. > More
AI threats to security. > More
Urgent security upgrades are needed at hospitals - NOW ! > More
Super Bowl security: Federal, state and Las Vegas officials ready vigilant measures > More
Hackers Abuse Google Search Ads to Attack IT & System Admins > More
What's in the Senate's proposed border security package > More
At Rally for Border Security in Texas, Fears of "Invasion" and "Civil War" > More
Lurie Children's Hospital in Chicago investigating cyber security matter as network down for 5th day > More
China's Hackers Keep Targeting US Water and Electricity Supplies > More
AI-generated videos a growing threat to elections, head of cybersecurity warns > More
Justice Department sues Texas over state's new border security law > More
US water utilities targeted by foreign hackers > More
House Homeland Security Committee sets first Mayorkas impeachment hearing > More
The biggest cybersecurity and cyberattack stories of 2023 > More
States and Congress wrestle with cybersecurity after Iran attacks utilities > More
Hackers Hijack Industrial Control System at US Water Utility > More
Cybersecurity Incident Hits Fidelity National Financial > More
General Electric Investigates Alleged DARPA Breach > More
KyberSwap Says Hackers Stole $55m > More
North Korean Software Supply Chain Attack Hits North America, Asia > More
Idaho National Nuclear Lab Targeted in Major Data Breach > More
Do not make these "5 dumb tech security mistakes" ! > More
UK and US develop new global guidelines for AI security > More
Biden steps up security for Jewish communities in the U.S. after the attack in Israel > More
Security chiefs got wind of something amiss in Gaza, thought it was a drill > More
Analysts Examine Israel's Security Failures in Hamas Attack > More
Large-scale Akira Ransomware Attacking Unsecured Computers > More
Why climate change is a national security risk > More
Google Initiates the End of Passwords, Making Passkeys the Default for Users > More
Stabbing attack at Atlanta Airport leaves 3 hospitalized > More
Famed hacker and Twitter whistleblower Peiter 'Mudge' Zatko is joining the Biden administration > More
More Schools Hit By Cyber-Attacks Before Term Begins > More
Artificial Intelligence: Transforming Healthcare, Cybersecurity, and Communications > More
Key Cybersecurity Tools That Can Mitigate the Cost of a Breach > More
Russian cyber-attacks "relentless" as threat of WW3 grows, expert warns > More
Tens of thousands of Connecticut residents have personal information scooped up in massive cybersecurity breach > More
A New AI-Based Honeypot to Engage Attackers as a Real System > More
Top security for 'jailbreak king' > More
The biggest cyber security incidents in August 2023 > More
A Ukrainian-made missile that could hit targets 930 miles inside Russia is nearly ready, says top security official > More
Electoral Commission failed basic security test before hack > More
TSA Updates Pipeline Cybersecurity Requirements > More
Security Breaches Are on the Rise and Your Identity Isn't Safe. Here's How Verified Identities Can Help > More
New SEC rule requires public companies to disclose cybersecurity breaches in 4 days > More
Multiple Security Issues Identified in Peloton Fitness Equipment > More
Laptops will need to support growing AI and security priorities, says Lenovo > More
U.S. House Republicans from Texas target federal funding unless Homeland Security chief is removed > More
The REAL reasons behind the strict rules at airport security, from removing laptops from bags to separating liquids (and how to get through the checkpoint faster) > More
UFOs " What the Government Calls UAPs " Present a Clear Threat to U.S. National Security, Former Military Pilots, Intelligence Officials Say > More
Biden nominates veteran national security official as top cyber adviser > More
The top 10 technologies defining the future of cybersecurity > More
Top cybersecurity tools aimed at protecting executives > More
A Cybersecurity Wish List Ahead of NATO Summit > More
Hackers have stolen $3 billion in crypto > More
ChatGPT's Trust and Security Dilemmas > More
5 ways to prepare your cybersecurity team for a crisis > More
Global Retailers Face Cyber Risk > More
Here's How To Protect Your Google Account > More
Senate to receive classified brief on AI threats and national security > More
Raging border crisis is a matter of national security > More
Automotive Cyber Security Market Size to Reach USD 30 Billion by 2032 > More
Massive cybersecurity breach hits biggest US law firms > More
Best Home Security System of 2023 > More
Apple Patches Security Glitches in iPhones and iPads > More
Concerns for national security grow in Biden administration > More
How to protect your family from AI scams > More
TSA introduces new cutting-edge security technology > More
Google backs creation of cybersecurity clinics > More
The Importance of Multi-Factor Authentication in Healthcare > More
Here's How To Minimize Email Threats > More
Interested in investing in cybersecurity stocks? > More
DOJ launches cyber unit with national security focus as China, Russia threats mount > More
Artificial Intelligence And Cybersecurity: For Good Or Evil? > More
ChatGPT is about to revolutionize > More
TSA tests new facial recognition technology to boost airport security > More
Industrial Cellular Routers at Risk: 11 New Vulnerabilities Expose OT Networks > More
Cybersecurity-as-a-Service Market to Be Worth $46.6 Billion by 2030. > More
Inside the cybersecurity labs protecting U.S. critical infrastructure > More
The White House National Cybersecurity Strategy Has a Fatal Flaw > More
Chinese and Russian hackers are making moves. Here's how the National Security Agency is trying to counter them > More
Google Gets Court Order to Take Down CryptBot That Infected Over 670,000 Computers > More
5 Big Statements From Cybersecurity Leaders At RSAC 2023 > More
Cybersecurity Director Says "Buckle Up" for Generative AI > More
Suppliers are weak link in cybersecurity > More
Biden: Military, intelligence community taking new steps > More
The staggering Pentagon document leak has caused untold damage, including the exposure of long-worked assets and intelligence operatives > More
Microsoft released software updates to plug 100 security holes in its Windows operating systems and other software, including a zero-day vulnerability that is already being used in active attacks. Not to be outdone, Apple has released a set of important updates addressing two zero-day vulnerabilities that are being used to attack iPhones, iPads and Macs. > More
Looking for a New Security Technology? Choose a Partner, not a Vendor > More
Western Digital Hackers Demand 8-Figure Ransom Payment for Data > More
Russia-Linked Hackers Launches Espionage Attacks on Foreign Diplomatic Entities > More
Microsoft Warns Accounting, Tax Return Preparation Firms of Remcos RAT Attacks > More
One of China's most popular apps has the ability to spy on its users....it's not TikTok! > More
Do this quick Google account security check now! > More
US Defense Department Launches "Hack the Pentagon" Website > More
Cyberattack disrupted access to its Microsoft Office 365 apps > More
Watchdog Bans OpenAI's ChatGPT Over Data Protection Concerns > More
New Money Message ransomware demands million dollar ransoms > More
Biden-Harris Administration Announces National Cybersecurity Strategy > More
Join Prosegur at ISC West, booth #14099, find out more about exciting plans for 2023 and beyond! Click here and enjoy a complimentary exhibit hall registration as our guest (saving you up to $150!). > More
Google has stepped in to remove a bogus Chrome browser extension from the official Web Store that masqueraded as OpenAI's ChatGPT > More
AMAG Technology Announces Integration with RealNetworks > More
Join AMAG at ISC West March 29-31 in Las Vegas, Booth # 14089. Enjoy complimentary exhibit hall registration as our guest (saving you up to $150!). > More
TikTok to be blocked > More
Charles Chuck Andrews Discusses His Amazing Journey from Police to Security In Texas > More
2023 Cybersecurity Maturity Report Reveals Organizational Unpreparedness for Cyberattacks > More
Cybercrime Losses Exceeded $10 Billion in 2022: FBI > More
How A Satellite Hack Became a Cybersecurity Wakeup Call > More
Experts discuss water, food security > More
Top 10 Growth Stocks in Cybersecurity > More
China flexes muscles in Latin America in latest security challenge to US > More
Is a World War by miscalculation or by mistake inevitable? > More
Cybersecurity in the Connected Medical Future > More
White House Allocates $3.1bn to Cybersecurity in New Budget > More
Google Reveals Alarming Surge in Russian Cyber Attacks > More
MyloBot Botnet Spreading Rapidly Worldwide: Infecting Over 50,000 Devices Daily > More
Five Cybersecurity Tips For Small- And Medium-Sized Enterprise > More
Clock ticking on food-security. > More
Homeland Security Committee to hold first field hearing on border crisis > More
Here's What 10 Cybersecurity CEOs Are Prioritizing In 2023 > More
Cybersecurity - Outlook for the Main Threat in the Digital Economy: Challenges, Stakes and Solutions > More
TikTok: It's hip, it's fun and it's a security risk > More
Google Reveals Alarming Surge in Russian Cyber Attacks > More
MyloBot Botnet Spreading Rapidly Worldwide: Infecting Over 50,000 Devices Daily > More
Five Cybersecurity Tips For Small- And Medium-Sized Enterprise > More
Clock ticking on food-security. > More
Homeland Security Committee to hold first field hearing on border crisis > More
Here's What 10 Cybersecurity CEOs Are Prioritizing In 2023 > More
Cybersecurity - Outlook for the Main Threat in the Digital Economy: Challenges, Stakes and Solutions > More
TikTok: It's hip, it's fun and it's a security risk > More
U.S. Federal Agencies Fall Victim to Cyber Attack Utilizing Legitimate RMM Software > More
Microsoft's security arm is now a $20 billion per year business > More
Please see our news archive for more breaking news about security solutions, homeland security, and security stocks... click here.